Israeli Hacker‘The Analyzer’Indicted in New York

Israeli hacker Ehud "The Analyzer" Tenenbaum was indicted Tuesday by a federal grand jury in Brooklyn on felony charges of conspiracy and fraud.
Between Feb. 2008 and May 2008 Tenenbaum and others engaged in a scheme to initiate transactions on account numbers belonging to other people, "to receive payment and other things" with an aggregate value of more than $1,000, the indictment charges (.pdf).
The U.S. attorney’s office in New York did not immediately respond to a call for comment.
Tenenbaum (shown at right in an old photo) achieved worldwide notoriety as a teenager in 1998, when he was caught pulling off a series of recreational intrusions into Pentagon computers, in an investigation the Defense Department code named "Solar Sunrise."
As reported here earlier, in September Canadian authorities announced they had arrested the now-29-year-old Tenenbaum and three Canadian accomplices for allegedly hacking into computers belonging to Direct Cash Management in Calgary, Alberta, which sells prepaid debit and credit cards through various merchants, and increasing the cash limits on those cards.
Then he and others allegedly withdrew CN$1.8 million (about U.S. $1.7 million) on the cards through ATMs in Canada and other countries. The arrests followed a months-long investigation by Canadian police and the U.S. Secret Service.
Canadian Crown prosecutor Jane McClellan described for Threat Level at the time how the alleged scheme worked. A number of people purchased 37 prepaid debit cards with small cash limits on them — usually CN$15. Then tracking data encoded in the magnetic stripe on the back of the card was allegedly passed to Tenenbaum.
That tracking data contained the account number and the customer PIN that allows the cardholder to withdraw cash from the account. Tenenbaum, alone or with the help of others, then allegedly hacked into Direct Cash’s server using a SQL injection attack and deleted the limits on some cards and increased the limit on other cards to a combined total of more than CN$3.5 million. The amount on one card account alone was increased to more than CN$1 million.
The card track data was then given or sold to others around the world who encoded blank cards with the data and used it to withdraw cash on the accounts. Within days CN$1.8 million had been stolen.
Direct Cash discovered the problem when it conducted a weekly audit and noticed that CN$1.4 million was missing. A subsequent forensic audit of its system revealed that someone had used a SQL injection attack to hack the company’s server.
McClellan said that Tenenbaum and people associated with him were caught on ATM video cameras withdrawing some of the cash soon after the cash limits on the cards were changed.
Tenenbaum was facing six counts of fraudulent use of credit card data and one count of fraud over $5,000 in Canada. He initially remained in custody in Calgary without bail, even though the three other suspects — Priscilla Mastrangelo, 30 (whom Tenenbaum identified as his fiancee), Jean Francois Ralph, 28, and Sypros Xenoulis, 33 (Tenenbaum’s partner in a computer security business) — were released on bond.
Then a court granted him $30,000 bail. But before Tenenbaum could leave the Calgary jail, U.S. authorities obtained a provisional warrant ordering Canadian authorities to retain him in custody, presumably while the grand jury in New York met to examine the evidence against him in the United States.
Tenenbaum was 19 when he was arrested in 1998 along with several other Israelis and two California teens in one of the first high-profile hacker cases that made international news. Tenenbaum and his fellow Israeli hackers referred to themselves at the time as the Israeli Internet Underground or the "Enforcers." According to Israeli court documents, their activities began when one of the Israelis asked Tenenbaum to help him hack the computer system of the Sde Boker Seminary to read the e-mail correspondence of a female.
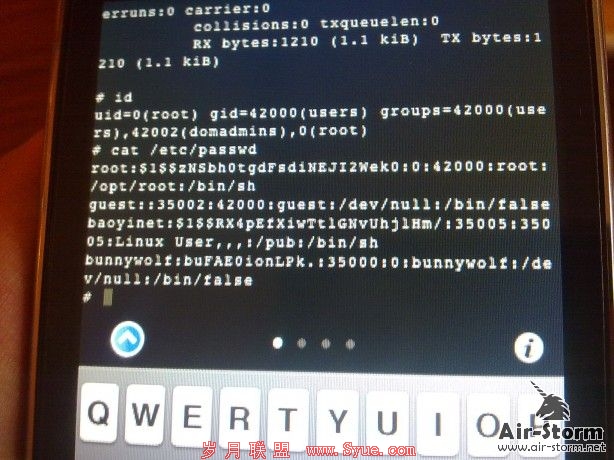
Tenenbaum then used sniffer and Trojan-horse programs to break into computer systems belonging to two Israeli ISPs and obtain user names and passwords of customers. He used the hijacked customer accounts to breach other computer systems belonging to all of the universities in Israel, the websites for the Israeli parliament and Israel’s president, and a system belonging to Hamas, a militant Palestinian organization. An attempt to breach the computer system of the Israel Defense Forces failed.
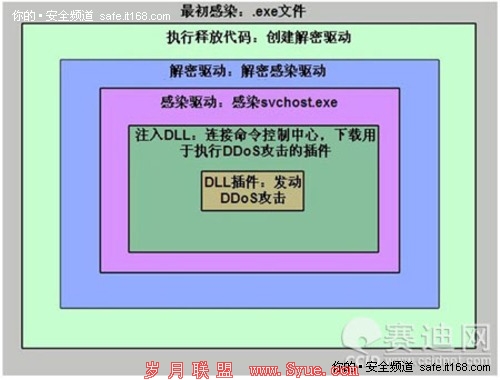
Tenenbaum, who referred to the California teens as his pupils, taught his accomplices how to hack into U.S. systems and gave them sniffer and Trojan programs to assist them. Although Tenenbaum’s attacks were unsophisticated — they simply exploited a long-known vulnerability in the Solaris operating system that had been left unpatched — he and his cohorts were nonetheless able to breach systems belonging to the Department of Defense, the Air Force and Navy, NASA, MIT, and several U.S. Ivy League universities.
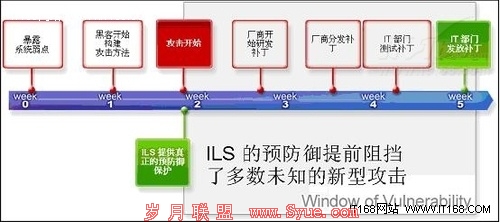
The attacks on the U.S. military systems came at a time of high alert in the Middle East when Iraqi President Saddam Hussein was defying U.N. weapons inspections. U.S. authorities were so unsettled by the breach of military computers — which they called "the most organized and systematic attack" that had occurred to date — that a joint investigation was launched by several government and military agencies, dubbed Operation Solar Sunrise, to track down the source of the threats.
Tenenbaum was caught after the two California teens were arrested.
UPDATE: Bob Nardoza, spokesman for the U.S. attorney’s office in the Eastern District of New York, told Threat Level that Tenenbaum is still in custody in Canada and the U.S. will be starting extradition proceedings shortly. He doesn’t know how long that will take.
As for the U.S. charges against Tenenbaum, he has no information other than what’s already in the indictment.
“It’s not a very extensive indictment,” he said.
He would not say whether the office anticipated additional arrests in relation to Tenenbaum’s case but said the investigation is ongoing.