linux下https的搭建总结
来源:岁月联盟
时间:2012-05-05
一:CA服务器的搭建[root@zzu ~]# yum install openssl*[root@zzu ~]# cd /etc/pki/[root@zzu pki]# vim tls/openssl.cnf45 dir = /etc/pki/CA88 countryName = optional 89 stateOrProvinceName = optional 90 organizationName = optional136 countryName_default = CN 一些默认选项141 stateOrProvinceName_default = beijing 一些默认选项144 localityName_default = beijing一些默认选项[root@zzu pki]# cd CA [root@zzu CA]# mkdir certs newcerts crl 创建3个目录和两个文件[root@zzu CA]# touch index.txt serial www.2cto.com [root@zzu CA]# echo "01">serial 根索引文件[root@zzu CA]#openssl genrsa 1024 >private/cakey.pem 创建ca的私钥文件[root@zzu CA]# chmod 600 private/cakey.pem 改变私钥的权限[root@zzu CA]#openssl req -new -key private/cakey.pem -days 3650 -x509 -out cacert.pem 为ca产生一份证书二.为www服务器颁发证书[root@zzu ~]# cd /etc/httpd/[[root@zzu httpd]# mkdir certs[root@zzu httpd]# cd certs/ [root@zzu certs]#openssl genrsa 1024 > httpd.key 产生服务器的私钥[root@zzu certs]# openssl req -new -key httpd.key -out httpd.csr产生服务器的请求文件[root@zzu certs]# openssl ca -in httpd.csr -out httpd.cert 产生服务器的证书文件[root@zzu certs]#cp /etc/pki/CA/cacert.pem ./ 拷贝ca的证书文件[root@zzu certs]#chmod 600 *[root@zzu certs]#yum install mod_ssl*改变文件的权限增加安全性[root@zzu certs]#vim /etc/httpd/conf.d/ssl.conf 捆绑证书文件和钥匙文件112 SSLCertificateFile /etc/httpd/certs/httpd.cert www.2cto.com 119 SSLCertificateKeyFile /etc/httpd/certs/httpd.key128 SSLCertificateChainFile /etc/httpd/certs/cacert.pem
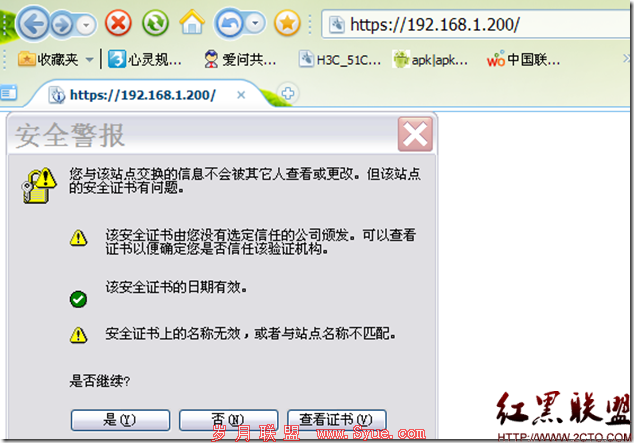
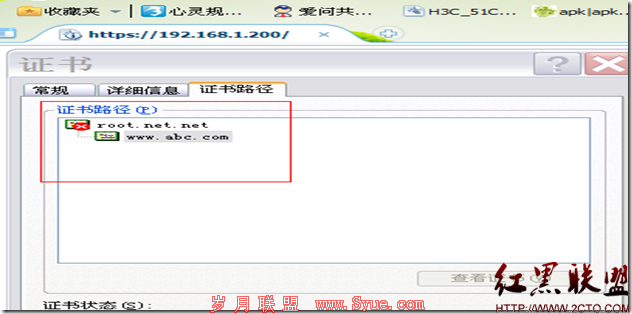
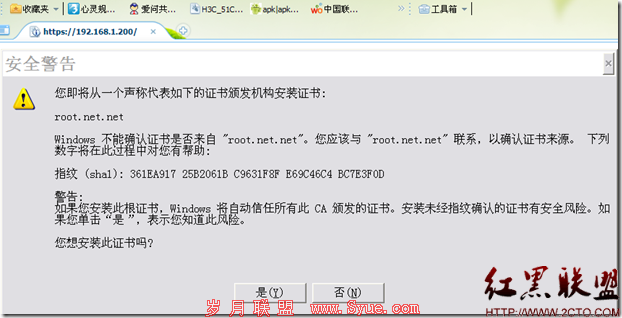
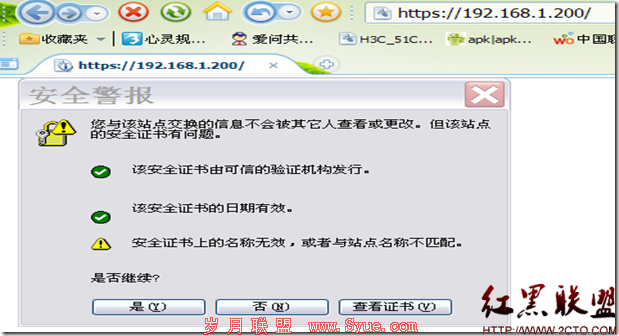
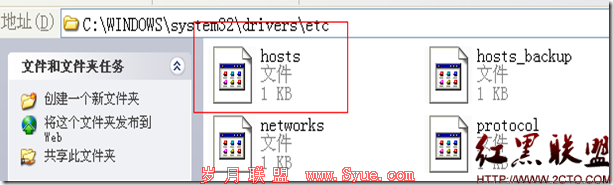
192.168.1.200 www.abc.com
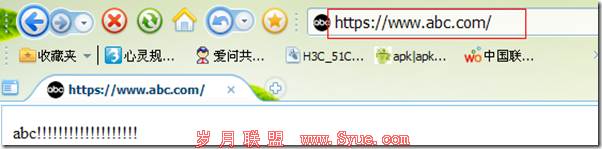
[root@zzu certs]# netstat -tupln |grep httpd tcp 0 0 :::80 :::* LISTEN 5544/httpd tcp 0 0 :::443 :::* LISTEN 5544/httpd
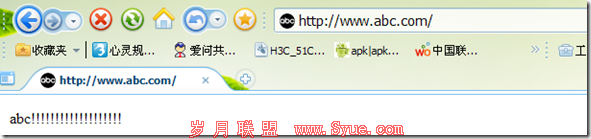
关闭原来的80端口[root@zzu certs]# vim /etc/httpd/conf/httpd.conf134 #Listen 80 注释掉该行[root@zzu certs]# service httpd restart Stopping httpd: [ OK ] Starting httpd: [ OK ][root@zzu certs]# netstat -tupln|grep httpd tcp 0 0 :::443 :::* LISTEN 5483/httpd
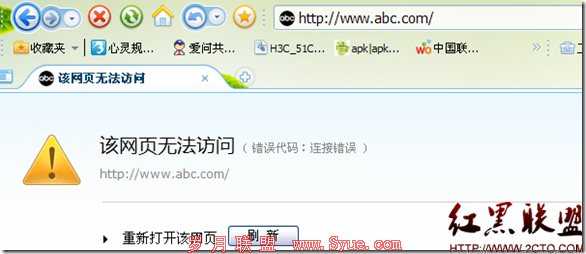
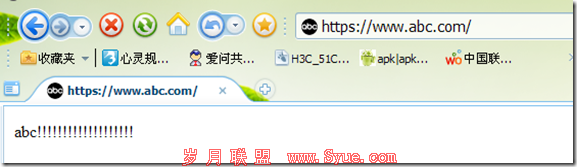 这样www.abc.com 就只能够使用https进行访问啦 补充:一:为www.abc.com 颁发证书192.168.1.200的主机[root@zzu certs]#vim /etc/httpd/conf.d/ssl.confnameVirtualHost 192.168.1.200:443<VirtualHost 192.168.1.200:443> DocumentRoot "/var/www/html" ServerName www.abc.com:443 ErrorLog logs/ssl_error_log TransferLog logs/ssl_access_log LogLevel warn www.2cto.com SSLEngine on SSLProtocol all -SSLv2 SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM:+LOW SSLCertificateFile /etc/httpd/certs/httpd.cert SSLCertificateKeyFile /etc/httpd/certs/httpd.key SSLCertificateChainFile /etc/pki/CA/cacert.pem <Files ~ "/.(cgi|shtml|phtml|php3?)$"> SSLOptions +StdEnvVars </Files> <Directory "/var/www/cgi-bin"> SSLOptions +StdEnvVars </Directory> SetEnvIf User-Agent ".*MSIE.*" / nokeepalive ssl-unclean-shutdown / downgrade-1.0 force-response-1.0 CustomLog logs/ssl_request_log / "%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x /"%r/" %b" </VirtualHost> 二:为 tec.abc.com 颁发证书192.168.1.100的主机[root@zzu certs]#vim /etc/httpd/conf.d/ssl.conf<VirtualHost 192.168.1.100:443> DocumentRoot "/var/www/tec" ServerName tec.abc.com:443 ErrorLog logs/ssl_error_log TransferLog logs/ssl_access_log LogLevel warn SSLEngine on SSLProtocol all -SSLv2 SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM:+LOW SSLCertificateFile /etc/httpd/certs/httpd1.cert SSLCertificateKeyFile /etc/httpd/certs/httpd1.key SSLCertificateChainFile /etc/pki/CA/cacert.pem <Files ~ "/.(cgi|shtml|phtml|php3?)$"> SSLOptions +StdEnvVars </Files> www.2cto.com <Directory "/var/www/cgi-bin"> SSLOptions +StdEnvVars </Directory> SetEnvIf User-Agent ".*MSIE.*" / nokeepalive ssl-unclean-shutdown / downgrade-1.0 force-response-1.0 CustomLog logs/ssl_request_log / "%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x /"%r/" %b" </VirtualHost> 摘自 再别combridge 的BLOG
这样www.abc.com 就只能够使用https进行访问啦 补充:一:为www.abc.com 颁发证书192.168.1.200的主机[root@zzu certs]#vim /etc/httpd/conf.d/ssl.confnameVirtualHost 192.168.1.200:443<VirtualHost 192.168.1.200:443> DocumentRoot "/var/www/html" ServerName www.abc.com:443 ErrorLog logs/ssl_error_log TransferLog logs/ssl_access_log LogLevel warn www.2cto.com SSLEngine on SSLProtocol all -SSLv2 SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM:+LOW SSLCertificateFile /etc/httpd/certs/httpd.cert SSLCertificateKeyFile /etc/httpd/certs/httpd.key SSLCertificateChainFile /etc/pki/CA/cacert.pem <Files ~ "/.(cgi|shtml|phtml|php3?)$"> SSLOptions +StdEnvVars </Files> <Directory "/var/www/cgi-bin"> SSLOptions +StdEnvVars </Directory> SetEnvIf User-Agent ".*MSIE.*" / nokeepalive ssl-unclean-shutdown / downgrade-1.0 force-response-1.0 CustomLog logs/ssl_request_log / "%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x /"%r/" %b" </VirtualHost> 二:为 tec.abc.com 颁发证书192.168.1.100的主机[root@zzu certs]#vim /etc/httpd/conf.d/ssl.conf<VirtualHost 192.168.1.100:443> DocumentRoot "/var/www/tec" ServerName tec.abc.com:443 ErrorLog logs/ssl_error_log TransferLog logs/ssl_access_log LogLevel warn SSLEngine on SSLProtocol all -SSLv2 SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM:+LOW SSLCertificateFile /etc/httpd/certs/httpd1.cert SSLCertificateKeyFile /etc/httpd/certs/httpd1.key SSLCertificateChainFile /etc/pki/CA/cacert.pem <Files ~ "/.(cgi|shtml|phtml|php3?)$"> SSLOptions +StdEnvVars </Files> www.2cto.com <Directory "/var/www/cgi-bin"> SSLOptions +StdEnvVars </Directory> SetEnvIf User-Agent ".*MSIE.*" / nokeepalive ssl-unclean-shutdown / downgrade-1.0 force-response-1.0 CustomLog logs/ssl_request_log / "%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x /"%r/" %b" </VirtualHost> 摘自 再别combridge 的BLOG
下一篇:Linux vim全选功能的实现